Exploiting Web Applications with Metasploit
Metasploit is a comprehensive penetration testing framework designed to identify and exploit vulnerabilities in web applications and networks. It offers a range of tools and features tailored for the entire penetration testing lifecycle, from reconnaissance to maintaining access.
Understanding Metasploit
Metasploit, written in Ruby, is extensible, allowing users to build custom features via plugins. Developed by Rapid7, it's available as both an open-source framework and a premium version with advanced capabilities.
Regularly updated with new exploits from the Common Vulnerabilities and Exposures (CVE), Metasploit ensures users have access to the latest security assessments.
Components of Metasploit
Metasploit comprises several key components, each serving specific purposes in penetration testing:
Exploits
Exploits are pieces of code that leverage vulnerabilities in systems. Metasploit provides a wide range of exploits categorized as Active and Passive. These exploits enable testers to gain access to systems and perform tasks.
A piece of code that exploits a system vulnerability is called an exploit. The particular activities that these exploits carry out depend on how severe the vulnerability is.
Software vulnerabilities, hardware vulnerabilities, zero-day vulnerabilities, and other vulnerabilities can all be exploited. Typical exploits include SQL injections, buffer overflows, and other similar flaws.
You can employ any of the many exploits provided by Metasploit, depending on the vulnerabilities that are currently present in the target system. These escapades fall under one of two categories:
Active Exploits: These types of exploits operate on a target system, take advantage of it, grant you access or allow you to carry out a certain activity, and then terminate.
Passive Exploits: These types of exploits operate by waiting for a connection from the target system. Hackers frequently employ this tactic when requesting that you download software or data from the internet. When you do, you establish a connection with a passive exploit that is operating on the hacker's machine.
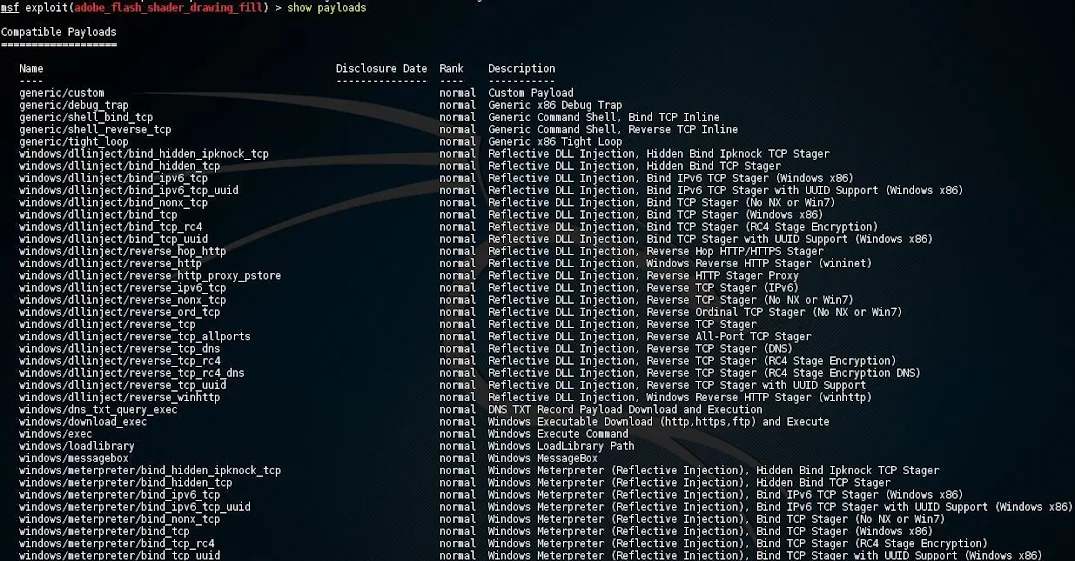
Payloads
Payloads are code snippets executed through exploits to achieve specific actions on target systems. Metasploit offers various payloads, including reverse shells, bind shells, and Meterpreter, for diverse exploitation scenarios.
A piece of code that runs through the exploit is called a payload. Payloads are used to carry out specific tasks, whereas exploits are used to gain access to a system.
For instance, you may combine an exploit with a keylogger as a payload. The keylogger will be installed on the target's computer if the exploit is successful.
A good selection of payloads, including reverse shells, bind shells, Meterpreter, and others, are available with Metasploit.
The majority of exploits may be used with a select few payloads, however it sometimes requires some investigation to determine which payload will be most effective.
After selecting an exploit, you may use Metasploit's "show payloads" command to get a list of payloads compatible with that exploit.
In Metasploit, there are various kinds of payloads. These three varieties are the ones you'll use the most in the end:
Singles are payloads, like keyloggers, that operate independently.
Stagers are payloads that cooperate with other payloads, such two payloads that work together to connect to the target and carry out a command.
Meterpreter is an advanced payload that can load and unload plugins at whim, resides in the target's memory, and is difficult to trace. I go into further depth on Meterpreter in the section below.
Auxiliaries
Auxiliary modules assist in performing custom functions beyond exploitation. These modules encompass tools like port scanners, fuzzers, and sniffers, enhancing the testing capabilities of Metasploit.
Modules known as auxiliary functions assist you in carrying out certain tasks other than breaking into a system. This covers fuzzers, sniffers, port scanners, and other tools.
The CERT auxiliary, for instance, can be used to search a network for SSL certificates that have expired. System administrators can automate certificate management with this.
You can write your own auxiliary if you know Ruby well. You can develop your own custom auxiliary module to do a weekly scan of a network for specific vulnerabilities.
After that, you can use it to scan your network rather than utilizing an already-existing scanner like Nmap.
Tools Offered by Metasploit
Metasploit offers a suite of tools to facilitate penetration testing:
msfconsole
MsfConsole serves as the primary interface for interacting with Metasploit, offering commands for executing tasks within the framework.
The default Metasploit interface, MsfConsole, provides you with all the commands you need to work with the Metasploit framework. Although there is a learning curve to become familiar with the CLI, once you do, it is very easy to use. Additionally, MsfConsole is the only way to access all of Metasploit's features.
Also, MsfConsole provides tab-completion for frequently used commands. Acquiring familiarity with the MsfConsole is a crucial step towards transforming into a Metasploit expert.
msfdb
msfdb is a database management tool integrated with Metasploit, enabling users to store and manage scan results, login credentials, and other data.
It is likely that you will require storage for your data if you frequently operate with huge networks. This covers the scan results, login information, and other details.
MSSFDb is a database management tool available in Metasploit. Using a PostgreSQL database as its foundation, msfdb provides you with a number of helpful tools for importing and exporting your findings.
You can import scan results from external programs like Nmap or Nessus using msfdb. Additionally, Nmap can be used to scan and import results within the msfconsole thanks to Metasploit's inbuilt db_nmap function.
msfvenom
msfvenom is a payload generator that creates custom payloads tailored to specific targets, increasing the success rate of exploitation attempts.
Lastly, we have msfvenom, which is a really cool name. Depending on your target, msfvenom allows you to create bespoke payloads.
One can make a target system somewhat secure by using a firewall or antivirus program. Because they are generic and apply to any system that falls under an operating system or service, existing Metasploit payloads may not function in such situations.
The two previous tools that Metsploit had, msfpayload and msfencode, were combined to create msfvenom. You can design and encrypt unique payloads for your exploits using msfvenom.
You can create your own payloads to increase the success percentage of your penetration test based on the extra details you know about the target.
Meterpreter
Meterpreter, an advanced payload, enables dynamic scripting on exploited systems, allowing for tasks such as encrypted communication, file operations, and privilege escalation.
In Metasploit, Meterpreter is an advanced payload. In contrast to other payloads that carry out a certain task, Meterpreter is dynamic and adaptable.
Here are some of the things you can accomplish if you can inject Meterpreter as the payload and exploit a system:
Create an encrypted channel of communication between the target and your system.
Extract hashes of passwords from the intended system.
Look through the target's filesystem for files.
File Upload/Download
Take pictures with your webcam.
Additionally, Meterpreter is quite discrete. Meterpreter is quite difficult to find because it resides in the target's memory. Meterpreter is difficult to track down with forensic tools as well.
Custom functions can be performed on the fly by writing Ruby Meterpreter scripts. Additionally, Meterpreter has a Python module that allows you to run extra commands on the target system in Python scripts.
Armitage
Armitage provides a graphical user interface for Metasploit, facilitating visualizations of targets and automated exploit recommendations.
Conclusion
Metasploit stands as a versatile and powerful framework for penetration testing, offering a comprehensive suite of tools and capabilities to assess and exploit vulnerabilities in web applications and networks effectively.



.png)








.jpg)










0 Comments